
Photo by Athul Cyriac Ajay on Unsplash
Let’s Encrypt is a Certificate Authority (CA) that provides an easy way to obtain and install free TLS/SSL certificates, thereby enabling encrypted HTTPS on web servers. It simplifies the process by providing a software client, Certbot, that attempts to automate most (if not all) of the required steps. Currently, the entire process of obtaining and installing a certificate is fully automated on both Apache and Nginx.
In this tutorial, we'll be installing SSL Cert on Nginx server running on Ubuntu OS.
Step 1 — Installing Certbot
The first step to using Let’s Encrypt to obtain an SSL certificate is to install the Certbot software on your server.
IInstall Certbot and it’s Nginx plugin with the below apt install commad:
$ sudo apt install certbot python3-certbot-nginx
Certbot is now ready to use, but in order for it to automatically configure SSL for Nginx, make sure that you have already created a server block config file for your domain. Then, please run the below command to verify the syntax of nginx configuration.
#To check server config file
$ sudo nginx -t
And then restart Nginx service with this command to effect the changes (whenever edited your domain config file, remember to restart the nginx service)
#To restart Nginx service
$ sudo systemctl restart nginx
Now we are ready to obtain the SSL cert from Let's Encrypt authority
Step 2 — Obtaining an SSL Certificate
Run the following command replaced example.com with your desire domain name
$ sudo certbot --nginx -d example.com -d www.example.com
If that’s successful, certbot will ask how you’d like to configure your HTTPS settings.
Output
Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
1: No redirect - Make no further changes to the webserver configuration.
2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for
new sites, or if you're confident your site works on HTTPS. You can undo this
change by editing your web server's configuration.
- - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - - -
Select the appropriate number [1-2] then [enter] (press 'c' to cancel):
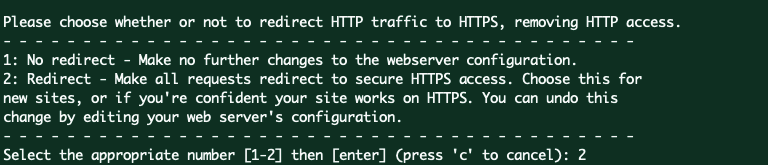
Most of the time, we'll need to redirect all requests to secure HTTPS, so, you would need to choose number 2 and press [enter]
to complete the cert installation process.
Once completed, you will see the following output message
Output
IMPORTANT NOTES:
- Congratulations! Your certificate and chain have been saved at:
/etc/letsencrypt/live/example.com/fullchain.pem
Your key file has been saved at:
/etc/letsencrypt/live/example.com/privkey.pem
Your cert will expire on 2020-08-18. To obtain a new or tweaked
version of this certificate in the future, simply run certbot again
with the "certonly" option. To non-interactively renew *all* of
your certificates, run "certbot renew"
- If you like Certbot, please consider supporting our work by:
Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate
Donating to EFF: https://eff.org/donate-le
Now our requested SSL cert is installed for the domain and the installation is completed.
Basically, certbot command will be automatically run the renewal process but we can make sure to check auto renewal process by the following command
$ sudo certbot renew --dry-run
If you didn't see any error, then the auto-renewal process is working perfectly and it'll renew before expiry. Let's Encrypt certificates are valid for 90 days and the auto-renewal process will run before expiry.